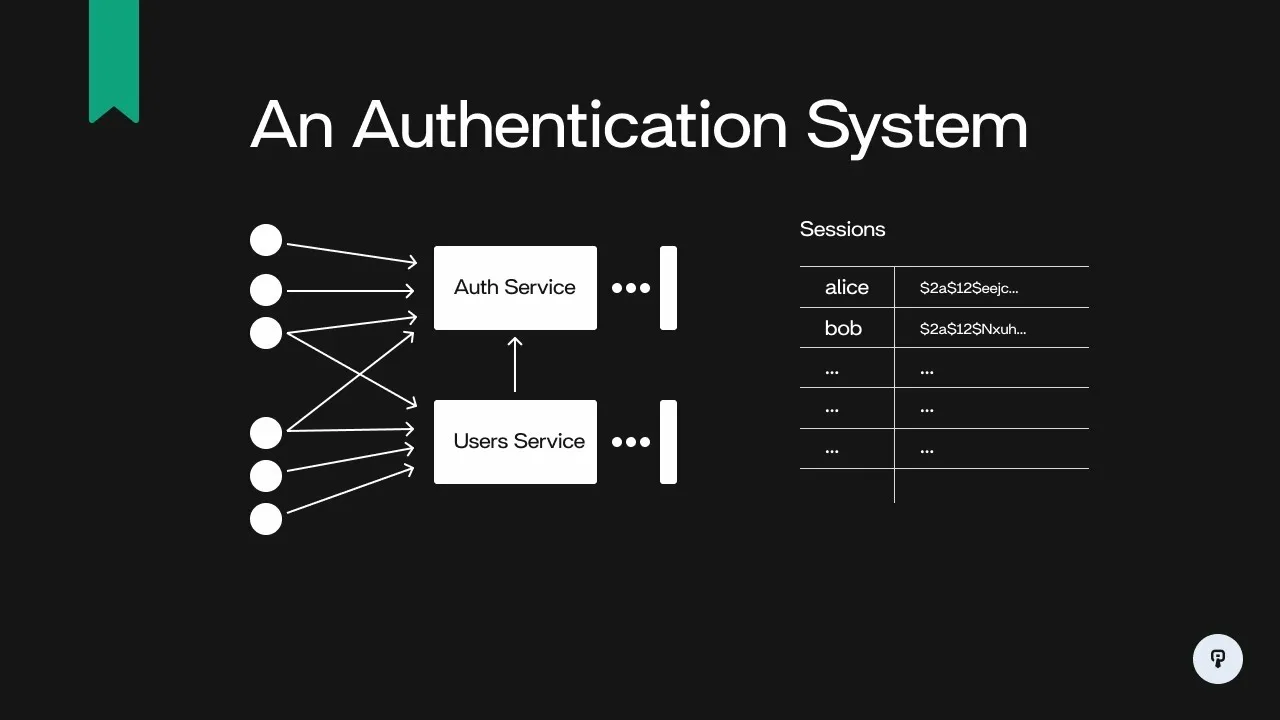
Secure authentication flows protect user accounts while preserving a smooth experience across devices and networks. Consumer apps face constant pressure to reduce friction during onboarding, yet attackers exploit weak identity checks at scale. Strong security emerges when teams design flows around realistic threat models, adaptive controls, and clear communication. The goal is not maximum friction, but proportional friction that rises when risk rises. By aligning protections with context, teams can improve both safety and conversion.
Risk-Based Decisions
Different actions carry different risk profiles. New devices, unusual locations, or sensitive changes warrant stronger verification. Adaptive authentication increases requirements when signals indicate elevated risk. This approach allocates friction where it matters most without punishing routine use.
Credential Hygiene and Recovery
Passwordless options, multi-factor authentication, and hardware-backed keys reduce reliance on weak secrets. Recovery flows deserve equal design attention because attackers often target them. Clear identity checks, rate limits, and monitoring deter abuse while protecting legitimate users from lockouts.
Telemetry and Continuous Improvement
Metrics on drop-off, recovery success, and suspicious activity guide iteration. Regular reviews align defenses with evolving threats and user behavior, improving outcomes over time.